Sentinel SIEM Cloud-native Security and Incident Management Services
Background Description
How do organizations generally manage security?
Traditionally, security operations have often been dominated by IT operations teams combined with a small number of security teams into a hybrid organization. However, this can lead to silos of security capabilities and responsibilities and may increase the number of security operations. cost and reduce its overall effectiveness. And a security operations center (SOC) is the next step in an organization's security evolution. It is a business-focused function made up of people, processes and technology. SOC continuously monitors, analyzes and responds to security threats through asset-centric operations based on log information. Among the components of establishing a SOC, security incident analysis and management (SIEM) solutions should be regarded as the core of the core.
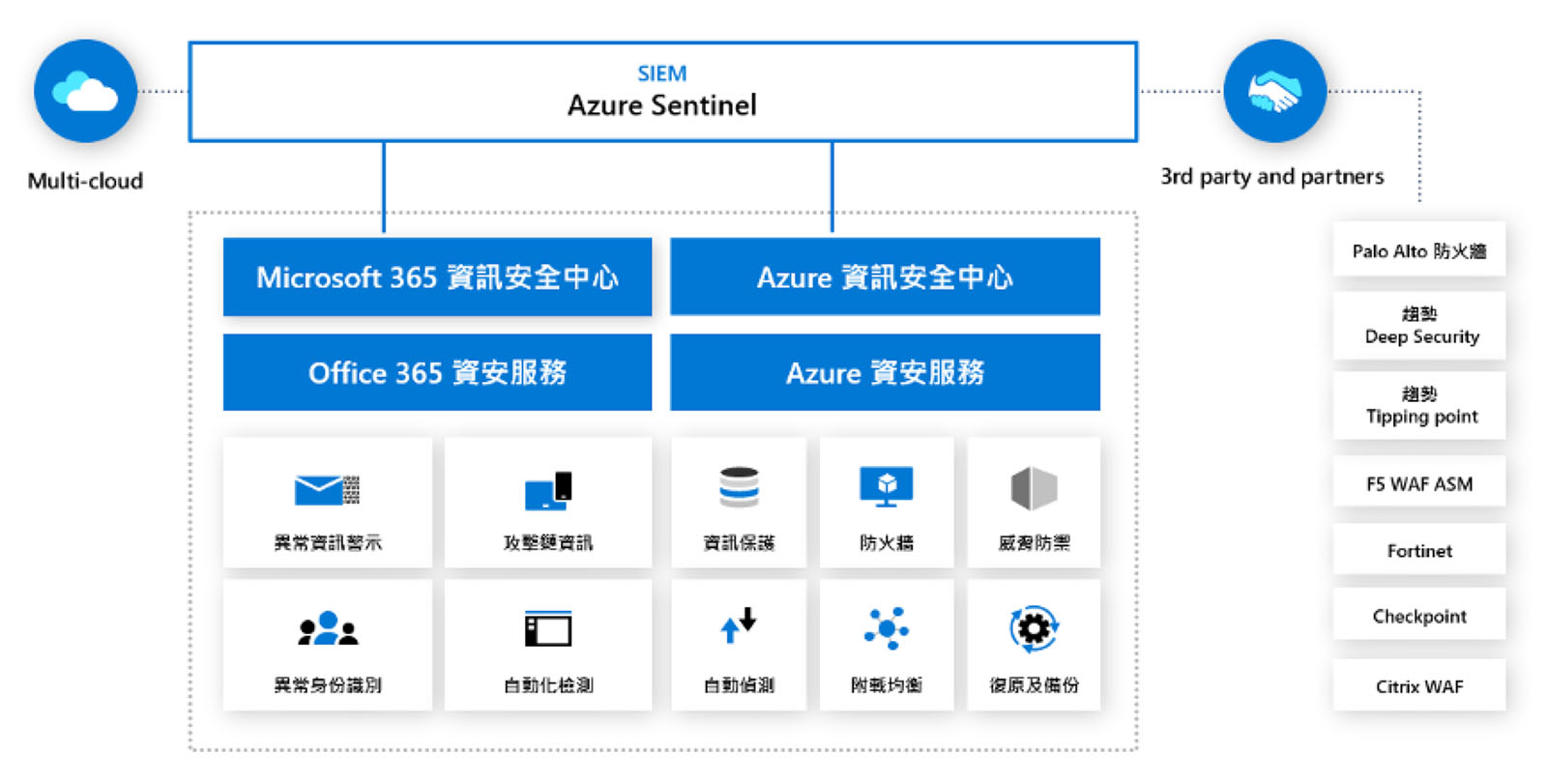
Microsoft Azure Sentinel is a Cloud Native SIEM solution using intelligent AI technology. It can provide complete security analysis for your entire enterprise and create a modern security operation center SOC. It uses intelligent proactive detection and analysis to discover and respond to increasingly complex security threats. Compared with traditional SIEM, it is more suitable for use in cloud environments. Based on years of cloud maintenance experience and cooperation with Microsoft, Acer eDC has become Taiwan's first cloud security monitoring service provider centered on the Azure Sentinel platform. In addition to outsourcing services in terms of promotion, Acer eDC also provides a simple cloud system integration Cloud SI service, which can assist enterprises in introducing planning, education and training, and optimization of detection rules.
Applicable Objects Include
manufacturing, financial services, retail and e-commerce, and new start-up companies.
Service Benefits
Based on research commissioned by Forrester Consulting, use Microsoft Azure Sentinel to automatically adjust to your organization's needs and only pay for the resources you need. Compared with the deployment of traditional internal SIEM, if you use Sentinel SIEM, which is cloud-native, the cost can be reduced by 48%, and the deployment speed can be accelerated by 67%. And achieved an ROI of 201% in three years.
Features
- What is Microsoft Sentinel and how does it work?
Microsoft Sentinel is a cloud-native security incident analysis and management platform SIEM that uses built-in AI to help quickly analyze large amounts of data across the enterprise. Microsoft Sentinel works from all sources including users, applications, servers and devices running on-premises and in any cloud. Aggregated data allows you to judge millions of records in seconds. It includes built-in connectors for easy wiring to popular security solutions. Collect data from any source using support for open standard formats like CEF and Syslog.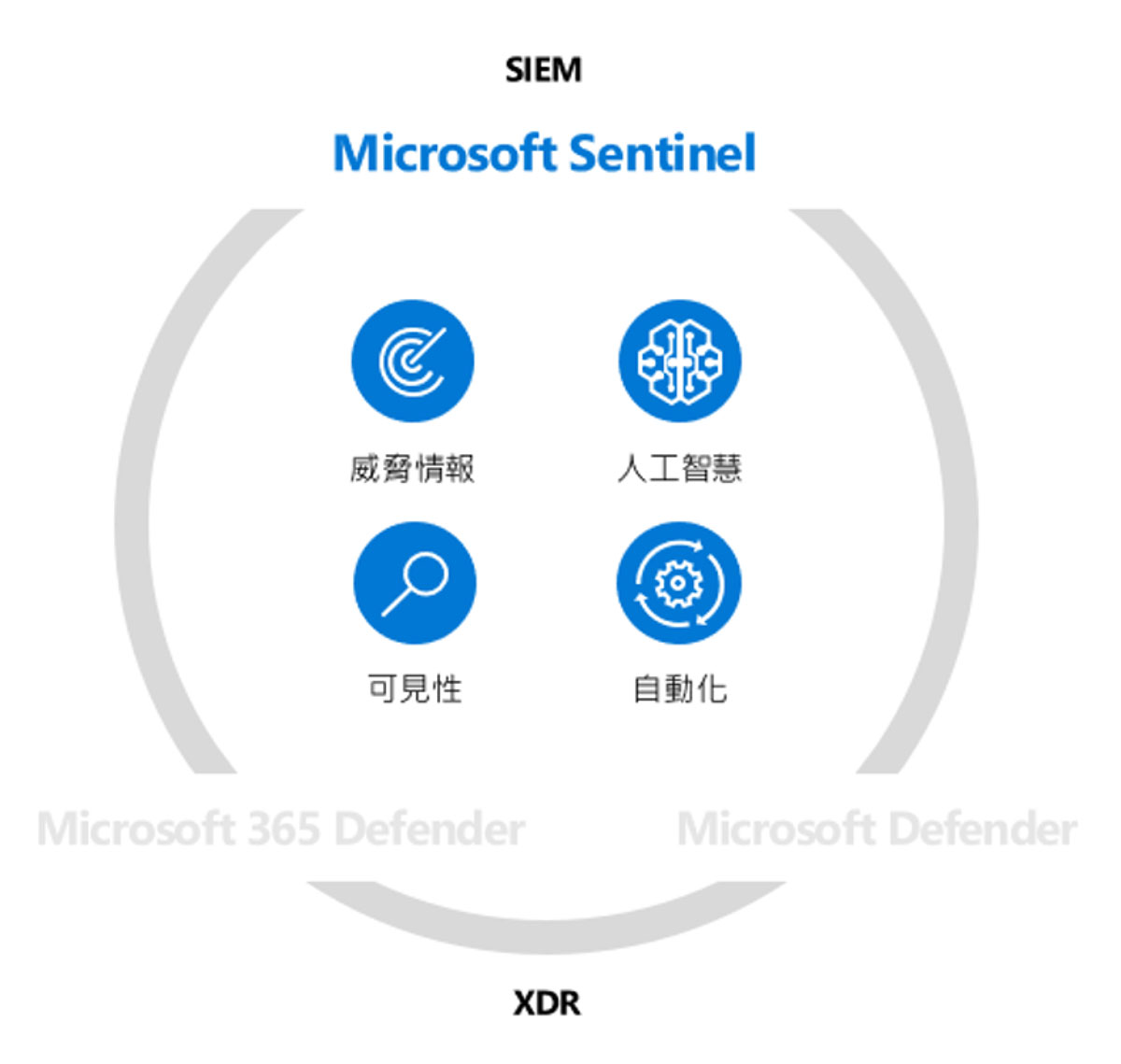
- Gain enterprise-wide security insights
With a cloud-native SIEM with best-in-class visibility and the ability to investigate attack chains. Collect security data at cloud-scale levels and integrate with existing tools. Use artificial intelligence to detect emergency threats and reduce false alarms by 79% within three years. Respond quickly with built-in scheduling and automation.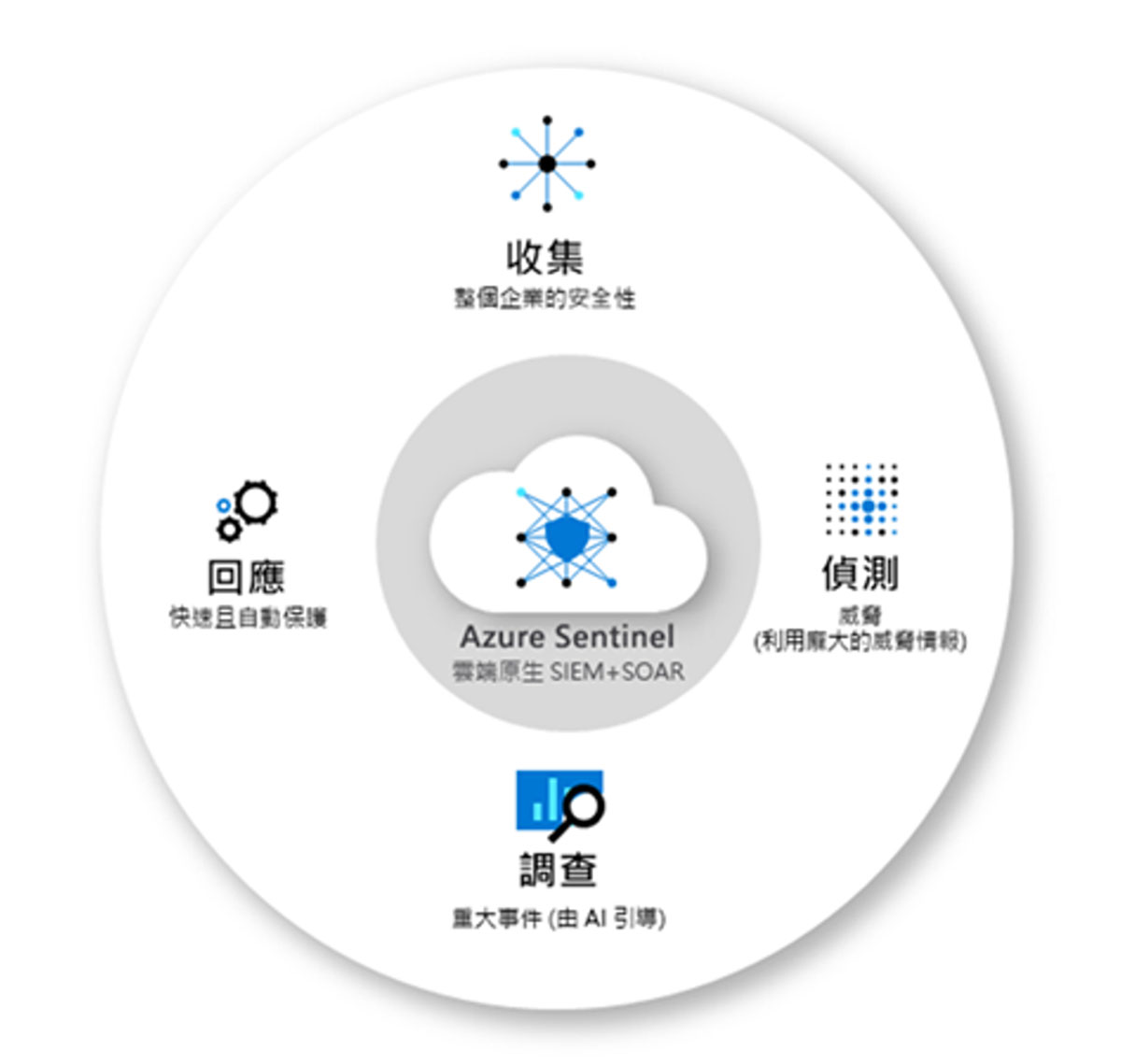
Function Introduction
- Collect Logs at Cloud Scale
Collect log data at cloud scale across all users, devices, applications and infrastructure on-premises and in multiple clouds. - Combined with Real-time Threat Intelligence Threat Intelligent
Preemptively detect previously undiscovered threats and reduce false positives with analytics and unparalleled threat intelligence built into Microsoft.
-
Intelligent AI Analysis Technology
Uses AI to investigate threats and hunt down suspicious activities on a large scale to delve deeper into network security efforts. Get the AI edge and focus on identifying real threats quickly. Reduce the noise from legitimate incidents and speed up proactive threat hunting using a built-in machine learning database based on daily analysis of trillions of signals. -
Automate the Security Orchestration Process to Respond to SOAR
using built-in common workflow orchestration processes and automation to quickly respond to incidents, view prioritized alert lists, obtain correlation analysis of thousands of security incidents in seconds, and integrate The entire range of each attack is presented visually. Automate and orchestrate common tasks and workflows to streamline security operations and speed response to threats. -
Leverage Continuous Behavioral Analysis UBEA
Leverages peer-to-peer analysis, machine learning, and built-in user behavior analysis to obtain more content and behavioral information for threat hunting and investigation to stay ahead of evolving threats. Achieve detection of unknown threats and abnormal behaviors of invaded users as well as internal threats. -
Comprehensive Data Collection Connectors
Using built-in connectors to simplify the collection of data from various sources, including Azure, on-premises solutions and different cloud providers. With simple setup, you can connect to data from Microsoft products. Import Office 365 audit records, Azure activity records and alerts, and analyze and draw correlations.