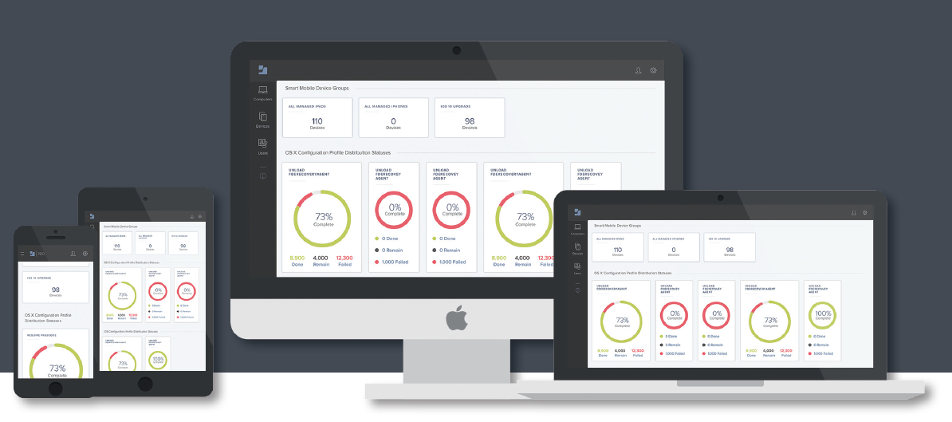
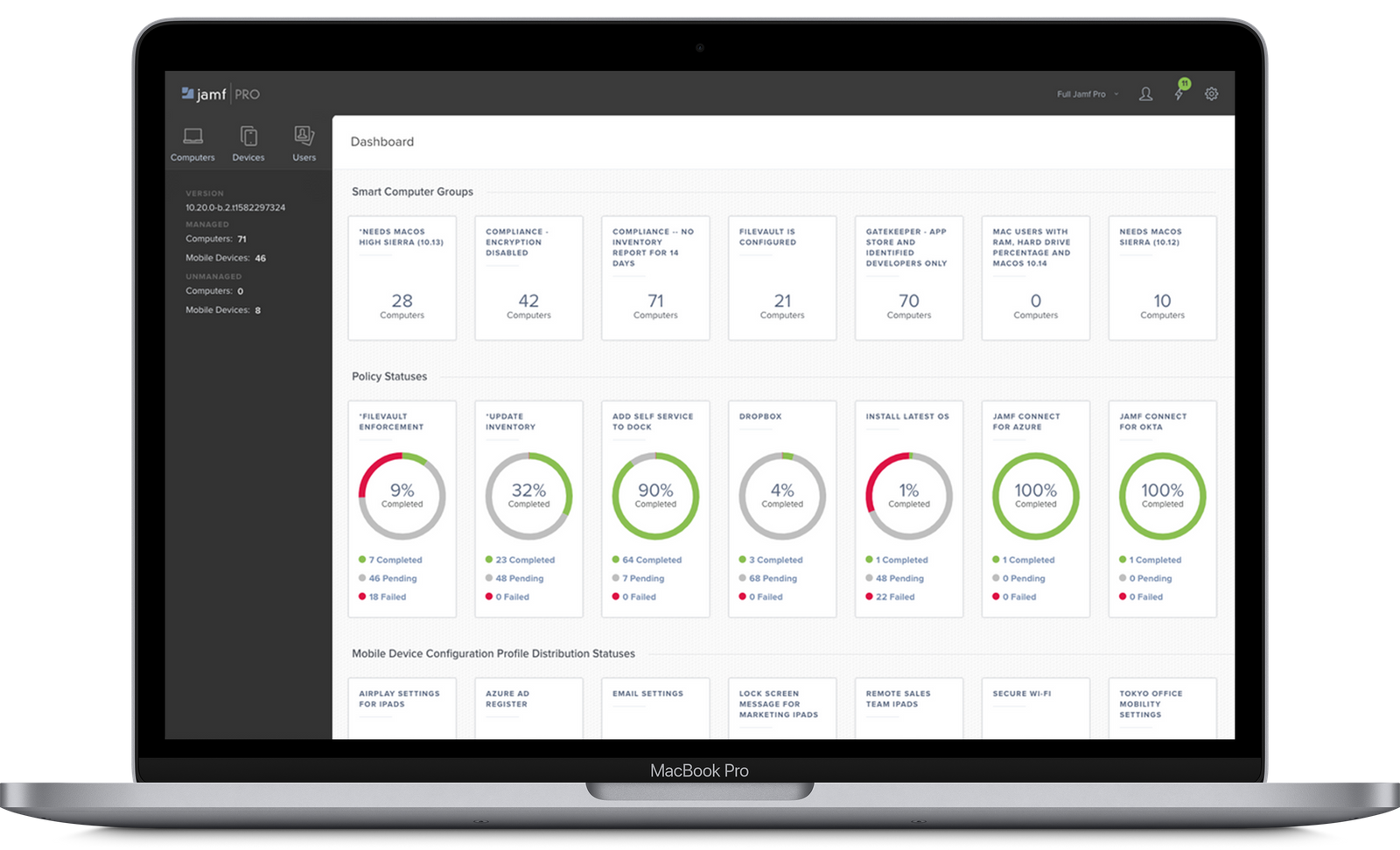
Jamf Pro mobile device management and endpoint protection solution
Acer eDC has joined the Jamf MSP partner program to help organizations successfully manage Apple devices and monitor security. We hope our solutions will make users safer and more powerful. If you have any needs related to Apple device management and security management,please feel free to contact us.
Background Description
Jamf solution goal is to help organizations successfully manage and protect Apple devices. It's designed to help organizations' employees regain focus so they don't have to waste time managing devices. With Jamf solutions, IT and security teams can confidently manage and protect end-user devices, data and apps. Jamf helps enterprises simplify device management workflows and achieve device management technology that is secure and protects personal privacy. Allowing companies to focus on developing their own technology.
Applicable objects:
financial services industry, educational institutions, technology service industry, and new start-up companies
Service efficiency
Why should you choose Apple Mobile Device Management Software (MDM)?
In order to allow users in a company or organization to access and instantly update the functions of the Apple device App, and to ensure safe use, there is an important reason why the organization needs a dedicated management of Apple device software. Enterprises and educational institutions can use Mac mobile device management (MDM) solutions. An excellent MDM platform allows employees to have personalized devices, allowing them to do more with less. MDM platforms automate repetitive management tasks and reduce human error to enhance security. Use Jamf to automate the Apple device management process and easily manage macOS and iOS devices, including Apple TV.
Quickly deploy MAC, IPAD and IPHONE.
You can integrate with APPLE's device registration solution to achieve deployment without touching the device.
Collect dynamic inventory
to monitor the allocation of hardware and software by user or device for more efficient planning and budgeting.
Reduce risk and protect resources
with world-class native security tools built into every device by APPLE.
Build an enterprise IT ecosystem
that maximizes the use of existing third-party tools, distributed through the cloud, and bundled within existing user directories.
Helping users do more—and do less—
our patented self-service applications provide users with one-stop, on-demand access to organization-approved apps, software and content. Allow their application systems to configure and run scheduled maintenance tasks without requiring IT staff.
Time-saving
remote lock and wipe capabilities, automatic patch updates, and backup status reporting ensure peace of mind.
Jamf Pro Mobile Device Management (MDM) Features
- Zero-touch deployment:As long as you register the device through "Apple Business Manager" or "Apple School Management", you can directly deliver the device from Apple to employees. IT staff can also use the excellent Mac device management system. There is also no need to manually configure the device. When a new employee logs in for the first time, Jamf will automatically configure the device and provide the apps necessary for work based on the employee's cloud identity credentials. Enjoy a safe and smooth onboarding experience.
- Upgrades and updates are handled from one place :Mac computers are managed from day one. Jamf's close partnership with Apple allows us to immediately support new versions of the operating system on the day it is released. Same-day support is important to maintaining productivity and safety. Jamf simplifies the upgrade and update process of Apple OS, remotely manages mobile devices and configurations, and automatically collects device data. Jamf's Apple MDM software keeps devices and systems operating stably and in optimal condition.
- Without a proper mobile device management platform, information security protection cannot be implemented.
Modern security management must be able to support the growing mobile workforce. Hackers are like thieves. They usually target places where doors and windows are not closed, such as unpatched software, old and unreliable networks, and hidden dangers caused by human error. Jamf's comprehensive management platform will not miss any potential crisis. It automatically logs inventory, deploys, deploys and manages patches to ensure every door and window is closed; it uses monitoring and malware protection as both a telescope and a shield to stay alert. Through zero-touch deployment, devices are automatically ensured to be regularly updated, patched in real time and maintained in an encrypted state, no matter where they are. Automated data collection tracks device status and alerts IT teams when updates are needed. Integrated endpoint protection prevents, isolates and remediates malware threats without slowing down end users. In terms of information security visibility and compliance, a single user cloud identity is used, and password policies and multi-factor authentication (MFA) are implemented every time you log in. Endpoint protection ensures the security of end devices and controls the entire device. data, even if the device is lost or stolen.
Function introduction
How can we develop security standards to manage Appe devices?
Before implementing Apple device management, we need to establish security standards and implement them. Referring to CIS is a good place to start. The full name of CIS is Center for Internet Security. It is a regular version of macOS security assessment that discusses eight aspects and is considered a complete checklist for managing Apple devices. Jamf Pro has complete corresponding methods in each aspect to meet the needs of information security. Consider.
Jamf Endpoint Protection (EDR) Features
-
Defend against new security threats: EDR tailored for Apple devices ensures that both organizational data and user privacy are safe. Proactively monitor for known or suspected threats and get instant notifications. Jamf's enterprise endpoint device protection service specifically designed for Apple devices can minimize risks posed by known or unknown threats such as malware or potentially unwanted apps. Its comprehensive threat prevention and remediation solutions execute without compromising device security, privacy or performance.
Jamf’s endpoint protection products offer:
- Advanced behavioral monitoring for suspected threats, such as exploiting vulnerabilities for inappropriate behavior.
- Device analytics means faster detection, notification and response to threats.
- Increase security visibility and compliance through detailed reports and real-time alerts.
- Enforce data policies to ensure only compliant storage devices are allowed.
- Automated remediation process to prevent suspicious threats from running on Mac and Apple mobile devices.
- Isolate malware to minimize damage.
- Take advantage of the latest threat intelligence from Jamf Threat Labs.
- Block unauthorized storage devices to reduce the chance of data leakage.
Jamf endpoint protection protects against threats from the inside out. Keep organizational data and user privacy safe.
Jamf Executive Threat Protection (MDR) Features
- •Provides more advanced detection and remote response capabilities, which can detect events or activities on mobile phones and tablets, and use appropriate and efficient tools to respond when an incident occurs. Attacks on mobile devices can also be seen at a glance.
- Defense in depth mechanism :Faster threat detection capabilities and repair system security. In order to strengthen defense against advanced attacks, device information and system logs can be collected to support comprehensive investigation operations. No matter how experienced the attacker is, he will still leave records, so it is more important to know how to find these clues.
Jamf Executive Threat Protection can:
- •Perform in-depth analysis to identify indicators of compromise (IOC).
- Automatically generate a sequential timeline of suspicious events, listing the time and reason why the device was compromised.
- Providing security teams with a clear and understandable summary of incidents can surface complex zero-day attacks that may have previously gone unnoticed.
- Provides security teams with built-in incident response tools to enable them to defeat advanced persistent threats, while continuously performing device monitoring to ensure that threats are eradicated and users are protected.